Dynamic Vlan Assignment Microsoft Nps 2012
This article outlines Dashboard configuration to use a RADIUS server for WPA2-Enterprise authentication, RADIUS server requirements, and an example server. Please refer to the following two Microsoft documents for instructions on adding the NPS role to Windows Server, and registering the new NPS server in Active.
I'm having same issue. Server 2012R2 Unifi AP-AC-PRO running 3.7.21.5389 Unifi Controller running 5.2.9 I've got Radius working fine with NPS as long as I don't try to use Dynamic VLAN via Radius.
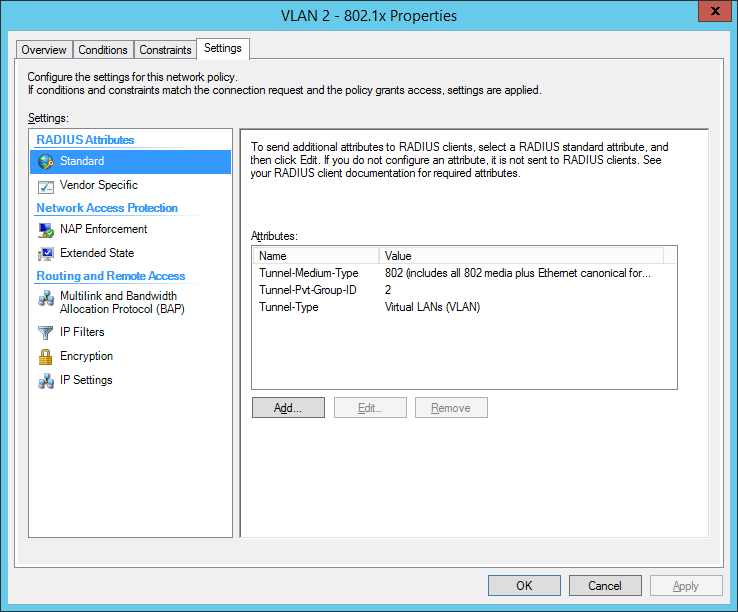
Radius Attributes I add are: Tunnel-Pvt_Group-ID = Tunnel-Type = Virtual LANs (VLAN) Tunne-Medium-Type = 802 Enabled Radius Assigned VLAN within Unif Controller. Looking at logs with debug mode on, on the AP, I see that Radius completes, and the AP understand that the client should be getting the correct VLAN as per the following being logged: Jan 15 13:09:05 UBNT user.warn kernel: [ 3262.410000] ieee80211_ioctl_setparam: VLANID32 = However, client doesn't get DHCP. I statically set the IP on the device and no change. Enabled port mirroring on the switch port that the AP connects to, and wiresharked that traffic, and never see any packets coming from the client computer in question (looked via IP and/or MAC address). Almost seems like the endpoints are put into limbo within the AP after RADIUS handshaking is completed.
Behavior is same regardless if it's an Android phone, or 2 different Windows 10 wireless laptops. I've also simply tried communicating (ping, etc) between the 2 laptops, with static IP's set, that should be on the same VLAN (and show as such via AP logs handshaking results, like what I listed above), and they can't communicate with eachother. I've also SSH into the AP, run tcpdump wide open (not restricted to a specific interface) and see zero of the traffic attempting to be generated from either of the laptops. I'm testing this with only a single SSID for simplicity. I've tried differing VLAN's too, no change. Wired devices do not have any issue, it's only wireless devices behind the AP. Only thing I've found from others with same behavior is regarding FreeRadius and needing to enable 'use_tunneled_reply = yes' to solve the problem, however I don't know how to do that within NPS or if that's even possible. The switch is trunked on thsoe VLANs.
The switch isn't stripping the VLAN tags, as I've wiresharked the feed from the AP and see ZERO traffic from the devices once they are assigned vlan via Radius. In addition, besides wiresharking, I've also ran TCPDUMP directly on the wireless access point and also see ZERO traffic from the devices once they are assigned the dynamic vlan via radius. It's not the switch. It's like the AP puts the devices into some kind of limbo/jail. If I go back to static VLAN per SSID, it works fine.
Hi, I'm having major issues getting IP assignment to pass over from my DHCP controller to clients that authorise and get assigned a VLAN from my NPS. I've researched for the past few days before posting here, both throughout the Unifi Beta Firmware post, Unifi Forums, here in SpiceWorks and in general and across the internet on Dynamic VLAN assignment setup, but there is seldom a mention of how to set this up when passing this between VMs on a physical host etc.
Apologies for this, but as my first time post, I could so with some pointers that anyone can give me:) ---------------------- I have a UniFi AC-LR with the installed [release-qca956x-3.6.x.136] which apparently allows RADIUS controlled VLAN assignment. The good news is that I have RADIUS authentication [and demonstrably the WiFi connection] working for users assigned to an Active Directory ‘Admin’ Group.
There is no VLAN settings in the RADIUS Attributes section on the NPS policy. I guess this is to be expected since there is no VLAN tag assigned to the SSID from Unifi (As per instructions on the beta firmware for dynamic VLAN to work) and therefore just goes straight through, on the default untagged VLAN.
Now this is where I have issues I have created a second policy for ‘Standard’ users, which DOES contain the VLAN settings in the RADIUS Attributes section. See this picture for settings I believe as far as these settings go, everything is correct (?) I can get wireless devices to authorise with the NPS server correctly (I can see in the Event Viewer logs that the user name in the assigned AD group is granted access) so clearly the NPS server is authenticating correctly.
But none of the clients get an IP address. This is where I’m having major difficulty and need some pointers (as many as possible!) in how to go about achieving the final stage of this setup. I’d like ‘Admin Users’ to get an IP address in the standard LAN range – 192.168.1.0/24 -- and I’d like ‘Standard Users’ to get an IP in a different range. Lets say – 192.168.20.0/24 --.20 for VLAN ease of identification, but I’m open to it being anything really if need be. This is the current layout of our setup Aside from the fact we have other VMs for other roles not pertinent to this diagram and other things connected to the HP 2920 Switch, this is the basic setup we have for Unifi.
• If I’m assigning a VLAN at the NPS server based on users’ Active directory group, do I still need to setup and mark the ports on the POE switch and the HP 2920 switch as tagged for the VLAN 20 ID? • If so, do I then also need to setup and mark the same VLAN tag on the ports used as the NIC team uplink to the virtual machine host? • Does both the NPS server and DC with DHCP need an additional virtual NIC adding with the subnet for each VLAN? If so, how do I then tell NPS to push a particular VLAN traffic through an adapter? • The DC with DHCP is (as far as I can tell) set up with the two different scopes.
One for current LAN traffic, and a new scope I’ve created – 192.168.20.100 to 192.168.20.200 – for the VLAN. How does the DHCP server know to assign this new scope to a particular VLAN? • I’ve read that this is somehow achieved via an IP helper address at the switch.
Do I just set this at the HP 2920 switch? Or the Unifi POE switch too? It seems as though once a user is authorised at the NPS, that traffic wouldn’t then exit back out to the physical switch and instead would just use the virtual switch inside the physical VM.?? • What commands either via CLI or web interface do I need to give to the HP switch if I *do* need to do this? I’ve followed other guides on the internet mostly relating to cisco switches.
The commands seemed to take on the CLI, but nothing worked. I’ve also got a similar setup at home with the same AP and firmware, VMs for NPS & DHCP etc, although I’m using HyperV and my switch is a Netgear GS724Tv4. That said, I’ve still ran into the same problems. I’m obviously missing something. I’ve dealt with VLANS before but never set them up from scratch, and certainly not tried to use the same port for 2 or more VLAN assignments and using NPS RADIUS to dynamically assign a VLAN based on groups. I’ve used RADIUS with NPS before and I’m quite proficient in Virtual Machine Host setup etc but VLAN setup is a new area to me. Any pointed anyone can give to help pass the new scope IP address over to the VLAN assignment when a client authorises would be IMMENSLEY helpful.
Where and I going wrong? What do I need to do?!?! I hope I’ve been clear enough, but if I do need to clarify anything, I will do. I've actually tried that once on my switch(es) but still came up against the same sticking point. I'm thinking this may be more down to the need to configure an additional adapter on the DHCP server by adding one through Xen Center? I'm sure I have all the ports appropriate for the routing configured to be in the correct VLAN.
The only other thing I'm thinking at this point is that because we have 2x switches which cross over with each other [ie: 1 NIC on the physical host connects to one switch and the second NIC connects to the second switch for bonding/redundancy] is that there is some missing config or something on the switch[es] to make them act as the same VLAN. FYI - I have added the truk links between them as part of the same VLAN. Figured this would be a definite requirement! @ita-tomi -- I've now set up the ip helper-address on the VLAN.
This was what I expected I needed to do - just needed to wait for authorisation. Download Video Woodstock 1999 Dvd. Ok so new problem with this. Actually not a problem per-se, but I need some explanations??
I was hoping someone can help explain something to me, or even tell me where I am going wrong, if indeed I am I have set up RADIUS authentication on a new VM with NPS on Windows 2012. So far so good – everything works beautifully. Admin users (the AD group assigned to the policy which is on the untagged VLAN) can connect with their AD credentials; I can see them authenticate and they get a DHCP address just fine. @ita-tomi Yes there is a working conenction between the switches and the DHCP server -- in so much as the switches connect to the physical host for the DHCP VM, and the rest of the client computers get DHCP just fine. The problem is: I have second AD group set up for other users. These users are dynamically assigned a VLAN by the policy of ’20’ Authenticating against the server with the standard user credentials and watching the console of the Wi-Fi shows that this passes through fine and the VLAN is indeed tagged. However – Users do not get a DHCP address.
(I have already set up a second scope on the DHCP server for this VLAN and configured all ports which lead to the bonded VM connections across both physical hosts and the trunk between the switches along with the uplink to the POE switch for the Access Points AND the AP POE switch itself as tagging VLAN 20 traffic on all the interconnected ports – As you would expect to be done for this kind of setup). But still nothing works. I should point out at this point that I have already configured the VLAN ID (20) across both the switches and via the CLI, added the IP helper address for this VLAN to be the main internal LAN IP of the DHCP server – 192.168.1.30. All that said (sorry for the long intro) – It wasn’t until I added a second virtual NIC to the DHCP server and told it the NIC (via XenCenter) it was on VLAN 20, that the entire process worked – Suddenly clients were able to connect with a DHCP address in the new scope I had specified. This is my question— Why though?? Everything I have read said that the IP helper address points to the single IP of the DHCP server that you use for your standard LAN.
Soft Start Switch For Power Tools. NOTHING about adding a new NIC on the VLAN ID in order to do that. Not to mention this new VLAN NIC has an IP in the VLAN range. Is this unique to the fact the DHCP server is a VM?
(Online guides do not distinguish, and given their prevalence these days, I wouldn’t think it matters anyway) I actually had to do the same at my home (as I have the same setup, albeit on HyperV) and I simply came to the conclusion it was due to my home switch being only L2 and not smart enough and not able to telnet into it and specify an IP-helper. I’m confused!! I’m pleased that its working, but I’d like to understand why this was required??
What if we needed 5 VLANs? Would I therefore need to add 5 separate NICs to the DHCP server to achieve the different IP scopes to each dynamically assigned device?
This doesn’t feel right:-/ Any pointers or explanations would be helpful. I’ll keep the configuration as-is for now whilst I work on gateway routing for this VLAN over a separate ADSL internet line, versus our main line. I've done quite few virtual Windows DHCP servers, there is no special configuration they need. They provide IP:s over MPLS, routed networks etc given that there is local IP Helper (or DHCP Relay, how you want to call it) and it has working connection to Windows DHCP server: routes and open firewall ports. I would say thet the IP helper setup for some reason does not work and things started to work out when you brought DHCP server itself into VLAN 20 so that itself answers directly to DHCP requests in VLAN 20.